Published on the 21/07/2017 | Written by Kyle Taege

Your guide to security planning, attack mode and the aftermath…advice for SMB by Kyle Taege…
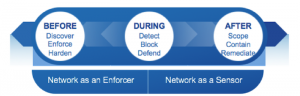
Cyber threats are more complex and more sophisticated than ever before. Attacks have adapted to take advantage of new ways of working (e.g. more mobile workers) but cyber security hasn’t kept pace with technological change. Common cyber security challenges for SMBs For small and medium-sized businesses across Australia and New Zealand, these challenges are amplified as security often takes a back seat to simply keeping operations running. But if you fall victim to a cyber-attack, it could put your entire business at risk. Dicker Data believes as businesses embrace the digital age, security needs to be driving the decision-making process to help deliver the right outcomes. Effective security is more than just a firewall But this can be so restrictive that it hinders operations, such as mobile workers being locked out of connecting to an organisation from outside a protected network because only on-site employees are granted access. Security now needs to act differently across all stages of the attack continuum (before, during & after). 9 steps to create an effective cyber security plan: During an attack – if a possible threat is allowed to enter, it is then monitored. After an attack Security for the digital age Cisco and Dicker Data have partnered to explore how cyber threats are changing and why solutions such as Cisco Umbrella are providing robust security for the digital age. ABOUT KYLE TAEGE// Kyle is the Networking Business Manager at Dicker Data NZ
Security used to take a blocking-focused approach which stopped anything that looked remotely malicious (or was unknown) from entering a network.
Cisco, a long-standing Dicker Data partner, has been known as a networking specialist but, over the past few years, it has acquired several security companies to expand their expertise and deliver a more comprehensive security stack. For small businesses who lack the in-house capabilities, outsourcing their security needs is an effective way to ensure these 9 steps are taken to future-proof the company.